Fraudsters leverage complex phishing scams in attempt to gain control over organizations’ Meta accounts
A sophisticated phishing campaign is targeting businesses of every size in an attempt to compromise Facebook and Instagram accounts with access to Meta Business Suite. Meta Business Suite, also known as Meta for Business, is a set of tools enabling organizations to manage their business’ presence on the Facebook and Instagram platforms. Access to Meta Business Suite is granted through an underlying Facebook or Instagram account. Adversaries involved in this threat have demonstrated a high degree of proficiency in attack obfuscation, victim selection, and advanced social engineering techniques. They also make use of generative AI in order to reliably generate several variations of the threat, making them more difficult to block. In this article we’ll explore the main ways adversaries leverage these accounts and the risks each pose. We’ll also discuss the set of techniques being leveraged by adversaries which makes this attack so dangerous.
What Makes This Campaign Compelling
The targeting of Meta for Business brings into focus the high value compromised businesses on social channels hold for cybercriminals. While individually-owned accounts are commonly the object of attacks, business accounts have the potential for a larger payout, broader reach, and less scrutiny. There are several risks that organizations may face from their social media accounts; let’s run through several of the most common.
Ad Fraud
Organizations with access to Meta Business Suite often use the platform’s considerable advertising prowess to market their offerings to the ocean of social media users. Adversaries who gain access to these accounts can hijack them to post ads to their own malicious offerings such as counterfeit goods or other scams. In addition to siphoning funds already attributed to advertising in the platform, adversaries may have less trouble getting a malicious ad approved when posting it under the guise of a compromised organization. Unlike the three other risks below, this threat is exclusive to businesses.
Impersonation
With access to an organization’s social media account, adversaries can attempt to use the accumulated trust and reach built up by an organization to spread misinformation, propagate further scams (as occurred during the infamous 2020 Twitter hack), or for other nefarious purposes. In addition to reputational damage, organizations may face considerable legal or regulatory risk if their social media presence is abused in this way. A major consideration for security practitioners is that this risk exists not just for official organizational accounts, but also for the personal accounts of executives and other high-profile individuals tied to the organization.
Data Harvesting
Some organizations may leverage their social media account for sensitive communications, either with end users via direct message or via closed groups. Adversaries who gain access to these organizations’ accounts are able to access this information and may seek to sell it or otherwise use it for further malicious purposes. The actual risk here will vary widely from organization to organization but is something important to consider for security professionals supporting an organization that heavily leverages social media. Like impersonation, security professionals should also consider whether this risk exists for the personal accounts of individuals within the organization.
Ransom
Fortra has observed instances in which an adversary will gain access to an organization’s social media account then lock the organization out of it, promising to restore access in return for a ransom. For companies which rely heavily on social media for marketing and advertising, this lockout can have devastating impacts on revenue. Smaller organizations without high level contacts at social media companies may struggle to regain access to their accounts via official support channels without paying the ransom and are most at risk to this cashout method. For larger organizations who may be able to use connections to regain access, this approach is less effective but may still be attempted in concert with a threat to post damaging information using the stolen account if a ransom is not received quickly.
The Tactics Behind the Campaign
Like many phishing threats, this attack is initially delivered via email. The adversary stays with a tried-and-true approach; impersonate a legitimate service (in this case Meta) and threaten the restriction or closure of the organization’s business account due to policy violations. The adversary also takes basic steps to reinforce their fake identity, including modifying the Display Name section of the “From”: banking on the fact that the majority of email clients show this value most prominently, and hide or minimize the actual sending address.
The adversary also makes use of generative AI technology. Fortra observed several variations of the email lure, subject, and Display Name. Fortra’s analysis strongly indicates that these emails were AI generated. This is a textbook example of the benefits generative AI can provide to cybercriminals; by generating multiple high-quality phishing emails with minimal effort it both lowers barriers for adversaries without strong language skills as well as enables adversaries to scale their operation more effectively.
The adversary also took pains to ensure that these malicious emails was delivered successfully. First, emails attributed to this campaign were sent using infrastructure belonging to legitimate sales and email marketing organizations. By leveraging the services of this reputable company, adversaries avoid deliverability problems caused by low reputation of their email infrastructure. This abuse of legitimate SASS capabilities is a variation of a living off the land attack known as Living off Trusted Sites (LOTS).
Additionally, steps were taken to disguise the malicious URL leading to the phishing website. The adversary leveraged a URL intermediary (in this case, Google notifications clicktracking), to mask the true destination of the URL. In many instances the adversary further disguised the URL by embedding it within a QR code. While neither tactic is new, both are increasingly popular means of hiding the intent of the URL. A growing number of phish are using QR phishing or Quishing as the primary lure in email attacks. At the time of writing, the volume of phish detected in this campaign using QR codes was more than three times greater than those using traditionally clickable links. In addition to making it harder for automated software to scan the URL, the biggest benefit of a QR code based lure is that the victim finishes the interaction on their mobile device, which is likely not protected by the organization’s cyber defenses.
An example of a lure containing a QR code-embedded link
When the victim clicks the Help Center button or scans the QR code, a notifications.google.com link redirects them to a phishing website masquerading as a Business Help Center page for Meta. Nearly all phishing websites observed in this campaign were hosted on lookalike domains to add additional believability to the scam.
Here’s where it gets interesting. Most phishing sites immediately prompt the victim for the key piece of information being sought, (in this case, username and password). This threat takes a different approach. The initial page prompts the victim to complete an “appeal form” requesting plausible information. As seen in the image below, the form avoids requesting information that most individuals would consider highly sensitive. This initial step serves several purposes; the most important of which is that it gets the victim engaged with the phishing website with a small, innocuous ask. This is important later.
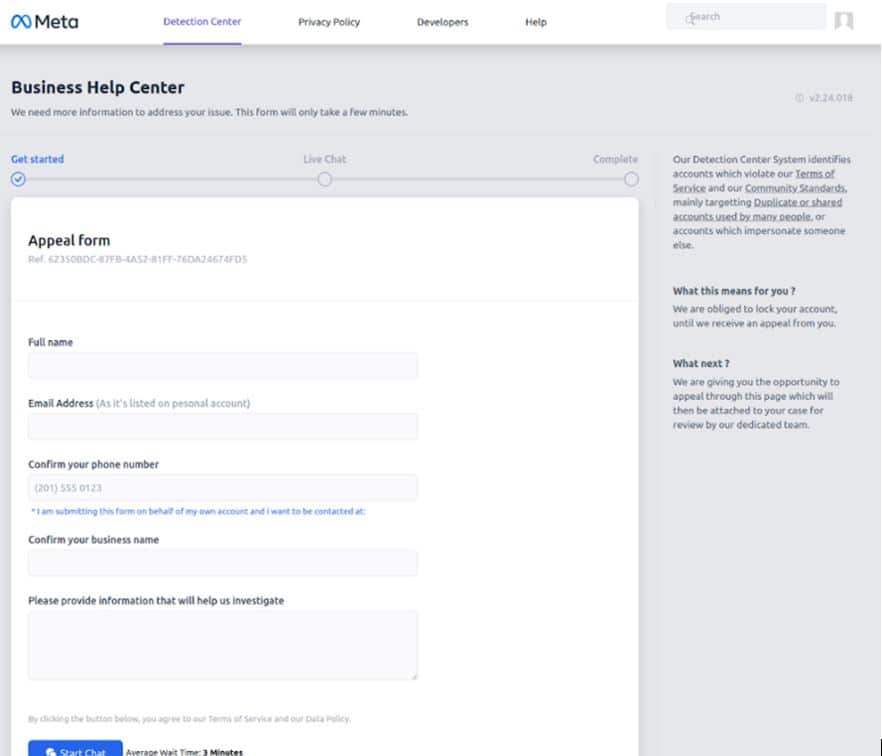
The first page of the phishing site
Once the form is complete, we see another unusual trait of the kit; the phishing site actually contains functionality to fake a live chat with an adversary impersonating a Meta support agent. In reality, the phishing site is communicating behind the scenes with a Telegram channel controlled by the attacker that they can use to control the phishing site. In the event that the adversary is not monitoring the phishing site when the victim visits, there is also functionality that automates most of the same interaction, though it is significantly less believable and barebones.
The victim is then briefly connected with a live threat actor impersonating Meta Support Staff to further engage the victim. Here’s where the trap is sprung; the victim is presented with an alert mid-chat that their session has expired. To resume the chat, they must log back in with their password. By delaying the ask for the sensitive piece of information and then suddenly requesting it, they get the victim engaged with the scam, and increase the likelihood that they will supply the password.
Once supplied with the password, the adversary will delay the victim while they test the credentials. If the credentials are invalid or two factor authentication is enabled, the criminal will further interact with the victim to bypass these obstacles before claiming that their appeal has been successfully submitted and they will receive further communication within a few days. In reality, the account has already been compromised.
How to Protect against this Threat
The targeting of Meta using multiple unusual and advanced tactics is a clear indicator of the value cybercriminals place on social media business accounts. Consider the following tactics to effectively defend against threats in this area.
- Best practices around Email Security and end-user Security Awareness Training are paramount. By using a multi-layered email security solution that can block malicious emails from being delivered to end users and educating end users on how to identify and report suspicious emails that evade security you greatly decrease the risk of having your credentials compromised
- Secure your organizations’ social media accounts using the most advanced identity features available to them (MFA, Security Keys, and unrecognized device alerts as of this writing).
-
- Consider directing executives or other high profile individuals to secure their own personal accounts in the same way.
-
- Limit access to account credentials to those individuals who absolutely require them.
-
- While not feasible in all organizations, an even more secure implementation is to consider having different individuals control different authentication factors. For example, have the main user of the account own the password, but a separate individual own the device which receives MFA codes.
-
About the Author
 Michael Tyler is the Senior Director of Security Operations at Fortra. Overseeing Managed Cybersecurity Services for the company’s Digital Risk and Email Security solutions, he also leads the Managed Threat Intelligence group supporting companies aiming to gain deeper understanding of adversaries targeting their organizations. With more than 15 years of experience in cybersecurity, Michael has a passion for uncovering the “why” behind attacker tactics and developing effective countermeasures to disrupt their operations. He also loves buffalo chicken pizza. Michael can be reached
Michael Tyler is the Senior Director of Security Operations at Fortra. Overseeing Managed Cybersecurity Services for the company’s Digital Risk and Email Security solutions, he also leads the Managed Threat Intelligence group supporting companies aiming to gain deeper understanding of adversaries targeting their organizations. With more than 15 years of experience in cybersecurity, Michael has a passion for uncovering the “why” behind attacker tactics and developing effective countermeasures to disrupt their operations. He also loves buffalo chicken pizza. Michael can be reached