Reading Time: 5 min
Are you worried about the legitimacy of the email alert you received from Microsoft?
Your concern makes sense as most of our important data is usually stored in a Microsoft account. If it is linked to any of your devices, it means that any attack on your Microsoft account can compromise the data in your devices as well.
In March 2024, according to research conducted by Statista, Outlook ranked third with around four percent of the total email views around the globe. To prevent data breaches, steps need to be taken to strengthen the security of Microsoft accounts.
This article will help you differentiate between authentic and fake Microsoft security emails and tips to spot emails that are fake or potentially malicious.
What is Microsoft Account Security Alert Email?
A Microsoft Account Security Email is an email received in your Microsoft account. It is sent as an alert by Microsoft when any suspicious activity is noticed. It helps account owners take immediate action and enhance their email security.
Microsoft uses security emails to share important updates with users. It is used to alert users about changes in their account information. However, as cyber-attacks are growing, these security notifications are also being forged and sent by scammers to trick Microsoft account holders. This has made several users around the world worried about their security.
Microsoft Account Team Email Scams
This is a type of phishing scam, in which an email appearing to be coming from Microsoft’s Account Team is in fact from a malicious source, impersonating the brand. These Email phishing scams are continuously increasing with the increase of online operations. These fake Microsoft Account Team emails are usually aimed at stealing the personal data of Microsoft clients and account holders.
These fake emails usually contain a spoofed email address or a logo similar to Microsoft. They cannot be detected easily as they look very similar to original emails from Microsoft support or the account team.
A sense of urgency is a defining factor for many of these malicious emails. The content is usually written to grab the user’s attention immediately. It may inform you about any suspicious activity on your account or instruct you to immediately change your password by clicking on a link.
Differentiating Between Authentic and Scam Microsoft Security Alert Emails
In recent years, scammers have gotten more advanced in sending phishing emails. To tell whether the security email received is legit or not, one must stay active and vigilant. If the email was sent from Microsoft, there is a high probability that other people have received it too.
Other than this, you can easily spot grammatical mistakes and errors in fake Microsoft Account Security Emails. Renowned companies like Microsoft will not leave room for such petty grammatical errors. You can also thoroughly read the content of the email (without clicking on any links or attachments) and observe the tone. Emails from official sources generally have a formal and professional tone. If not, it may be spam.
Common Microsoft Account Security Email Scams
With the advancements in security, cybersecurity threats are getting even more sophisticated. Some common threats include the following:
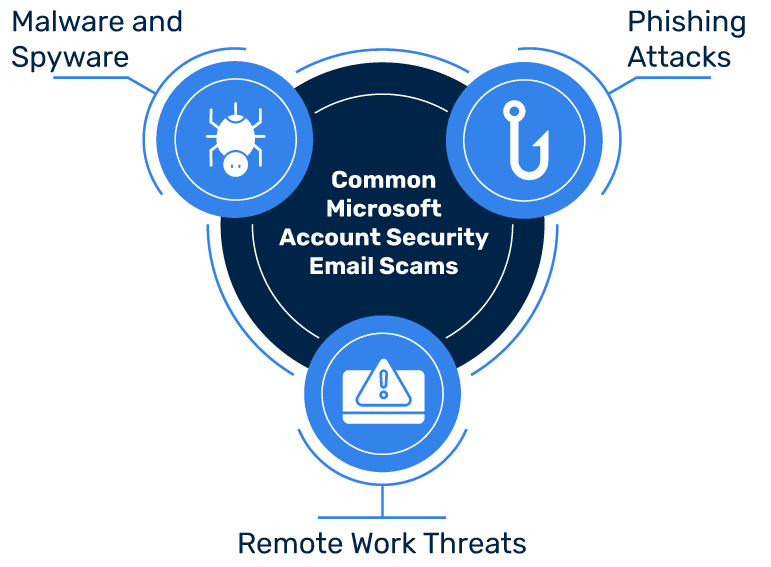
Phishing Attacks
Phishing is the most common attack targeting emails. It includes the use of malicious emails impersonating trusted sources with attached phishing links. These emails tend to draw personal or sensitive information from victims. Microsoft Account Security Email Scams may lead to phishing attacks.
Malware and Spyware
These are the malicious software that are designed to compromise your device and information. Malware can potentially disrupt your device’s functionality until resolved. Scam emails impersonating Microsoft support or account teams may aim at installing malware or spyware on your computer.
Remote Work Threats
With the increase in hybrid work mode, company networks are becoming wider and more complex. Employees often use their devices and insecure networks to access work files when working remotely. This enabled hackers to gain easy access to official company data. Employees must therefore be encouraged to strictly follow their company’s cybersecurity policy to protect confidential data and undertake email security training programs.
How to Tell if the Microsoft Account Security Alert Email Is Fake?
If you have received a fake security email before or are worried about being scammed in the future, here is what you must know to identify these emails:
Use Microsoft’s Security Features
Microsoft 365 provides tools to enhance email security. Its Spoof Intelligence feature in the Defender portal quickly detects spoofed emails. However, even with Microsoft’s advanced security features, some phishing emails may still go unrecognized.
Verify the Sender’s Information
When you receive an email under Microsoft’s name, don’t open it instantly. Cross-check the sender’s information and compare it to previous emails sent by Microsoft. Microsoft usually sends emails from @accountprotection.microsoft.com.
Recognize Microsoft’s Verification Indicators
Microsoft usually adds some indicators or warnings to emails that are not verified. These indicators may include a question mark on the sender’s image, highlighting the sender’s address with a tag, or flagging any other discrepancy. These indicators don’t necessarily mean that the email is fake. But it shows that you need to be careful before opening that email.
Notice Red Flags
Instead of blindly trusting the emails coming from a Microsoft Account, you must stay vigilant. Think about the reason behind you getting that email. If you received an email about any new update, confirm the same with other Outlook users. Big tech companies like Microsoft usually run a bulk email campaign for all users under such circumstances.
Best Practices for Your Microsoft Account Email Security
Whether you receive a security notification or not, you must work on the security of your Microsoft Email account before it is too late.
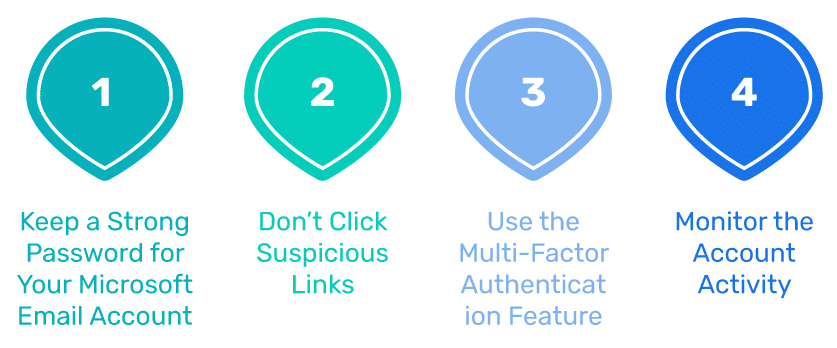
Keep a Strong Password for Your Microsoft Email Account
Unique and strong passwords act as the first line of defense in protecting your account. Adhere to Microsoft’s password recommendations. The password should ideally have a length of 12 to 16 characters and a concoction of numbers, uppercase and lowercase letters, and special characters.
Don’t Click Suspicious Links
Don’t believe all the emails received from an authority source. Even if you get an email from a Microsoft account, don’t open it instantly. If the email looks suspicious, is marked as spam, or doesn’t follow the original format, cross-check it for verification. Avoid opening any suspicious links attached to such emails.
Use the Multi-Factor Authentication Feature
Enable the Multi-factor Authentication feature on your Microsoft account as this adds another layer of protection to your email account.
Monitor the Account Activity
You can review the recent activity and login sessions on your Microsoft account through Outlook. Regularly checking your account activity lets you monitor and detect any suspicious activity. If you notice any suspicious source trying to log in to your account, disallow or remove it.
Businesses Can Improve Microsoft 365 Email Security with PowerDMARC
For Microsoft 365 users who use the portal for their email activities, there is PowerDMARC. We help businesses easily set up and monitor email authentication protocols. This can help them improve their domain security and deliverability over time while using simplified DMARC reports to identify emails being sent from unauthorized sources.
If you are an online business, start your 15-day free trial with PowerDMARC today!
*** This is a Security Bloggers Network syndicated blog from PowerDMARC authored by Ahona Rudra. Read the original post at: